
LateralAccessDevice
takes you back to before the Internet
How It Works | Download LAD | Support | LAD Security | Features & Uses | Resources | Members | User Guide
LAD at Work: LateralAccessDevice for BusinessLAD provides businesses great versatility in the areas of networking and communications, making it the one indispensable tool for network management, security and VoIP. Far-Flung Yet Close CommunicationsLAD's flexibility and versatility make it possible to seamlessly connect those working at home with the office (and vice versa) and amply accommodate hybrid work arrangements. With it's built-in SIP server engine, LAD connects telephone users not just locally, but globally. Any SIP-capable device, such as a VoIP telephone set or application-based SIP client, may be used with LAD's SIP server, via both local network connections and external Internet connections. Build your own VoIP PBX and enjoy LAD's practical call processing features, such as call holding queues, ring groups, conference rooms, cascading touchtone menus, extensions and more to create an integrated communications platform for your business, including integrating multiple locations into one unified VoIP PBX. 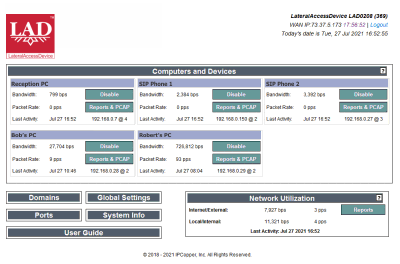
LAD's new device detection and client management and monitoring features provide network admins with robust visibility into network clients and their activity along with control and routing — all in one integrated, easy-to-use software package.Secure, Flexible NetworkingLAD delivers a number of sophisticated network monitoring tools for managing, investigating and monitoring local networks, including tools for new device detection, client management, activity monitoring and more. Monitoring takes place at both the network and individual client level, with customizable schedules for adapting levels of access to each client. LAD's reports and packet capture are accessible even to those with little experience, providing the benefit of a security camera for network communications and making it possible to investigate and prove what did or did not happen with the actual packets, as circumstances may require. LAD brings it all together seamlessly, making it easy to keep tabs on the workings of your business's computer network. LAD's DNS management neatly complements its packet capture and reporting features by making it possible to immediately act and simply cut off access to suspicious domain names to hinder malware and the like — just a simple click and bad domains have no way to reach into your network and your computers have no way to get to them. With its super-fast packet processing engine, LAD accounts for every packet, generating reports and making available comprehensive packet capture data, all-in-all providing unparalleled visibility into the data flows across and through networks, including both LAN-directed and WAN-directed data flows. Additionally, its integral LateralFirewall provides a way to control and filter both local and Internet traffic, key for building a more secure network. Support for Wi-Fi (2.4Ghz, 5G and 6G) gives you management, monitoring and control over both wired and wireless clients, allowing flexible use of the network while maintaining security and visibility into what goes on. Customization for Larger System Users and Service ProvidersLAD may be customized to address the specific processing, routing, data handling and other needs of larger users and service providers. Service providers (of Internet, VoIP and other data- or communications-related services) may use LAD customized for deployment in conjunction with the services they offer to achieve a wide range of goals. |